CYBER RISK: A COMPLETE GUIDE FOR PRIVATE FAMILIES

What is cyber risk management? How can I prevent identity theft? What can I do to protect my family from cybercrime?
There is nothing more important and more unknown than cyber risk. You can have your identity stolen, bank or brokerage accounts pilfered, even private information or secrets compromised. The cybersecurity threat is real and rapidly evolving. So let us discuss how to properly understand and address it.
This article is a primer for families and individuals which will provide a foundation of knowledge and best practices so you can be better protected from cybercrime. We specifically address family office cyber risk and insurance.

privateRISK: LEARN ALL YOU NEED ABOUT CYBER RISK MANAGEMENT
ADDITIONAL CHAPTERS IN OUR COMPLETE GUIDE
Understanding Cyber Risk
Cyber Risk is often thrown around as a blanket term to refer to
Defining Cyber Risk
What is the definition of cyber risk? We prefer a colloquial explanation– the potential for harm through the use of technology. After all, when you boil it down cyber risk is just like any other peril you have to manage.
The potential for harm caused through the use of technology.
~Robert P. Raymond, HUB International 6/22/2017
By looking at cyber risk through this minimalist lens, it is easier to envision where the risks are and what is at stake. Providing clarity among the various white noise and alarms currently circulating throughout the risk management & insurance industries.

Cyber Risk Is A New Peril
Cybersecurity, digital intrusion, cyber risk management–no matter what you call it, we are just having the same conversations we have had about countless risks before. Cyber risk is simply a new peril affecting the basic tenants of a family risk management strategy. It just feels more concerning because of how loud case studies are broadcast.
Cyber Risk deals with 3 basics areas within the risk management strategy:
- Financial Stability
- Privacy Concerns
- Personal Security
By distilling the risk into these 3 basic areas, we can more easily manage the risk, specifically family office cyber risk, through best practices, cyber governance, and cyber insurances.
WHAT IS A DATA BREACH?
Throughout this guide, you will find references to being breached. However, it is important to understand the difference between a breach and a security incident as this is the difference between a wake-up call and the potential for serious financial loss.
- Family Offices Reporting Breaches 15%
- Estimated To Be Actually Breached 40%
CYBER INCIDENT
A security event which compromises the integrity, confidentiality, or availability of an information asset
DATA BREACH
An incident which results in the confirmed disclosure of data to an unauthorized party
What Are The Perils Of Cyber Activity?
There are many reasons you may be the target or victim of cybercrime and many ways that you can be breached. If compromised, you can expect to suffer losses such as–
- Financial Loss
- Damage to equipment and infrastructure
- Opportunity Costs / Lost Deals
- Reputational Harm
These are just a few examples of ways you can be affected by cyber loss
Social Security Number
Breached
Email Administration
Clicking Bad Links
Email Administration
Clicking Bad Links
Smart Home Goes Bad
Google Home / Amazon Echo
A webcam, Google Home, or Amazon Echo device is compromised to listen/record you and your family
Fraud
Fraudulent Trade Instructions
Your email is compromised and used to send trade instructions to your investment advisor and funds are wired offshore
Ransomware
Malware Downloaded
CYBERSECURITY
Cybersecurity is a blanket term often thrown around to reference prevention of any type of digital intrusion. For private families, we consider this to be formally defined as- measures taken to safeguard your electronic data against unauthorized or criminal use.
The largest threats to your cybersecurity occur in three main areas:
- People
- Processes
- Technology
By understanding how each of these can expose you to risk you can better manage and protect yourself.
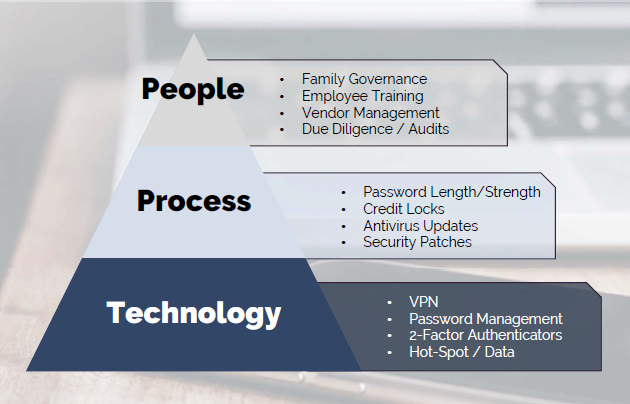
A look at the common weak points in your cybersecurity chain
WHAT IS TECHNOLOGY RISK?
The technology you utilize on a daily basis can either be your front line defense or an open door for cyber criminals. By assuring that you take prudent care in deploying and managing your technology risk, you will create a solid foundation for your cybersecurity. A few basic things to consider-
Utilize Antivirus Protection
By now, most people understand the importance of AV protection but it has never been more crucial for protecting your data and minimizing backdoor attacks.
Use A Data Hotspot and Avoid Public Wi-Fi
Yes, that fancy $800/night hotel has a password for its Wi-Fi but remember they give that out indiscriminately. The best way to safeguard your data on-the-go is to use your own personal cellular hotspot.
Enable Two-Factor Authentication (2FA/MFA)
Use of multi-factor authentication protocol is the easiest and most effective way to verify that the person accessing your data or systems is you.
Utilize A Password Manager
Most tech gurus will say the best way to store your passwords is in your brain, the next best is a little black book. However, they also concede that password managers do a fine job of encrypting your passwords and keeping you organized.
PROCESS RISK
Having set practices for managing your systems and processes will close a lot of the additional gaps in your cyber risk management strategy. Consider:
Update Your Software
Be sure to download and install the latest software updates for your devices, including operating systems, anti-virus/malware protection, or system-specific patches.
Use Appropriate Password Protocol
Just having a password is not enough. Each website or system should have its own unique password and each of those a complex string. Check out our password guide for more info.
Lock Your Credit
If you will not be needing your credit report to secure loans within the next 30 days, consider a soft lock on your credit report. For added security, consider a hard freeze.
PEOPLE RISK
The people in your ecosystem need to be in the know and properly trained in your systems and processes. This means family members, employees, and vendors.
Family Governance Strategy
When updating your family bylaws, be certain to include your family’s cyber charter. Outline your password requirements, software & systems, and outline all best practices you want to implement. Also, be sure to include your digital assets in your estate plan.
Employee Training
Aside from keeping your family up to date on your processes, you need to develop training designed to educate your staff on the do’s and don’ts.
Vendor Management
In some instances you may have control over training for your vendors, such as outsourced employees. Though in most cases you will need to include interview questions and contract verbiage in your vendor negotiations to both assure the firm is well versed in cyber best practices and willing to absorb the risks they may create in your relationship via insurance and indemnities.
Audits
None of the above is much good if you do not define process and intervals in which to test them. This means things such as penetration testing, reviewing your process protocol, and doing regular check-ups of software/hardware.
Cybersecurity is defined as: the measures taken to safeguard your electronic data against unauthorized or criminal use
How Vulnerable Are Family Offices to Cyber Risk?
Family Offices find themselves victims of targeted attacks for a variety of reasons:
Top Family Offices Cyber Risks
- Lax Security
- Access to Sensitive Information
- Mergers & Acquisitions Data
- Investment Positions
- Secret Information
Understanding Family Office Cyber Losses
- 15% of single family offices have reported breaches
- Estimated actual amount impacted is 40%, as they both underreport and do not understand when a breach occurs
- Average direct financial loss is $50,000
- Largest loss on record is $10,000,000
- It takes up to 250 days to identify a breach
- It then takes 50 days, on average, to fully mitigate a breach
Family Office Vulnerabilities to Cyber Loss
- Fame & Publicity
- Often Lack Formal Governance & Structure
- Fallacy That Privacy = Security
- Critical Data Is Accessible By Staff
- Lacking Investment In IT infrastructure
- Purposefully Sacrifice Security For Service, Speed, and/or Convenience
- Utilize External Vendors & Strategic Partners to Interface With Their Systems
HOW DOES CYBERCRIME CAUSE HARM?
In today’s connected world we move faster than ever. Unfortunately, that can leave us open to
Data
You cannot talk about cyber security without mentioning data. Whether your personal contacts & e-mails, log-in credentials for websites, or the latest draft of the company prospectus, all of your data is available and exposed.
Ransom & Extortion
Time
Technology & Devices
Legal
Interruption
Reputation
Regulatory Concerns
Crisis Response
THE EFFECTS OF POOR CYBER SECURITY
FINANCIAL
Regulatory Fines & Punitive Damage
Damage to IT Infrastructure & Devices
Loss of Revenue
LEGAL
Attorney General Fines & Penalties
Remediation Costs, SEC Audits
Civil & Class Action Lawsuits
REPUTATION
Reputation Damage / Public Relations
Customer Attrition
Loss of Senior Leadership / Board
TIME
Loss Of Operations
Opportunity Costs
Subscribe to our Newsletter
Get Breaking News, Trends, and Advice.
privateRISK.org
Personal Cyber Insurance
With cyber risk management being both a hot topic and a cottage industry, there are a lot of variables when it comes to insurance.
What Does Cyber Insurance Cover?
Cyber insurances protect your family against a wide array of loss, including-
Systems Attack / Malware
If your devices are damaged by malicious software, your insurer will provide data recovery services and hardware replacement.
Cyber Extortion / Ransomware
Should your systems be taken and a ransom demand
Digital Fraud
Should a bad actor access your accounts and steal funds, your insurance will reimburse you.
Identity Theft
If your password, social security number, or other personal information is taken your insurance will provide identity monitoring, rebuild your credit, and investigate where the theft may have originated from.
Cyber Liability
If you are a victim of digital intrusion which spreads to other family, friends, or business associates, the right insurance program will protect you against any legal liability to arise from other party’s data breach, invasion of privacy, or extortion.
Cyber Bullying
If you or a child is the victim of
What Are The Limitations Of Personal Cyber Insurance?
Like any insurance, this is a reactive response, so we always counsel investment into your people, process, and technology before stressing insurance. However, there are a few additional
Government Fines & Penalties
As individuals, you are unlikely to suffer fines related to a breach but operating as a family office, particularly if you manage money for other parties, can land you in some hot water which may not be covered by insurance.
Bodily Injury
In some instances with certain insurers,
Employees Devices
If an employee of
Vendor Restrictions
Without pre-planning your crisis response, you may find that your vendors are not on the approved list with your insurer.
How Does Cyber Insurance Integrate with Family Offices?
Family Office Cyber Risk Management requires a multi-layered approach beyond insurance. You must plan for the family office operation, the individual households within the family, and any businesses which are intertwined within. As a basic blueprint you need to address the following:
Private Family Cyber Insurance
The overall insurance program and risk management strategy for each family branch and generation
Family Office Cyber Insurance
Coverage for the office itself intended to respond for fraud, social engineering, or other crime perpetrated against the office and the staff
Commercial Risk Strategy
Outside of the family office operation, if there is a closely held business, or a business which overlaps into the family office (think- shares staff) then a strategy must be discussed on how to respond to a crisis on either side of the business
Family Cyber Governance
Without pre-planning and a dedicated family strategy, there may not be insurance to respond for all scenarios. More importantly, the proverbial chain will be weakened if a family branch or individual is not adhering to best practices and implementing an insurance program aligned with the rest of the family.
Carrier Positions on Personal Cyber Insurance
Not all families are the same and not all insurers offer appropriate protections for private family cyber liability or cyber property loss. Here is a breakdown of the carriers offering comprehensive solutions. Remember, you can always refer to our insurance carrier guide to learn more about choosing the right
Chubb Family Cyber Insurance
As a leader in personal insurance, Chubb has created cyber insurances which seamlessly integrate into your existing program.
PURE Starling Cyber Insurance
PURE was first to market with a cyber product specific for private families.
AIG CyberEdge Cyber Insurance
AIG was an early innovator in the personal insurance cyber risk space by adapting its successful and broad commercial solutions to families.
Additional Considerations For Cyber Risk Management
Non-Insurance Solutions For Your Family
Insurance is a great tool to help make you whole and shift the financial burden from your balance sheet to the insurance company. However, a great broker or risk manager will add additional value to your planning by addressing a few other key areas-
Existing Breaches
What good is insurance if you are actively breached? You should consider penetration testing or other cybersecurity audits to determine if you have a privacy issue you may not be aware of.
Device & Network Security
As previously discussed, technology is an integral part of prevent cyber loss. Be sure your device firmware and software are up to date. If using private servers, be sure your firewall is secure and set up redundancies to backup data. Current backups are an invaluable asset in the event of data loss or ransomware.
Public Relations Strategy
While not strictly a need in your cyber risk planning, this is an ideal time to revisit your crisis response strategy to prevent reputational fallout from a breach or other incident.
Digital Estate Provisions
Many people do not ready the End User License Agreement (EULA) for their favorite digital content provider like iTunes, Spotify, Amazon Kindle, etc. So, you may be surprised to know that the media you “purchase” is unlikely to transfer ownership to your spouse or next of kin–unless you specifically plan it in your will. Get your attorney to handle this.
Travel Habits
One of the easiest ways to become a victim of malware, hacking, or ransomware is through use of an unsecured network. This is quite true of airport lounges, hotel guest wifi, and even some countries which monitor all data transmitted via their internet service provides. Consider travelling with your own data hotspot, in addition to being secure, the cellular signal is much harder for a hacker to compromise.
Personal Security
Sometimes, you can be compromised by good, old fashioned, brute force. For high profile persons, having a security detail or security planning can go a long way. Get risk analysis and planning for your homes, offices, and travel itineraries.
Additional Learning
As you continue learning about managing property risk, the additional chapters in our guide will prove to be invaluable resources.
Check back for our PROPERTY RISK analyzer
Check back for the release of our property risk analysis tool.
Additional Learning
As you continue learning about managing your personal cyber risk, the additional chapters in our guide will prove to be invaluable resources.
Be the first to KNOW
Get Breaking News, Trends, and Advice
privateRISK.org




